ContainerX burst onto the container platform technology scene all the way back in 2016 and have since continued to provide a complete and efficient container-as-a-service platform that is available on both Windows and Linux devices, being highly accessible for anyone who requires a program to easily manage their software containers.
ContainerX’s first beta was all the way back in November of 2015. This beta allowed the team there to smooth out any kinks in their service and create the most efficient version of their product before official worldwide release to the public. The team itself consisted of talented engineers from many high-end, reputable technology companies such as VMware, Microsoft and Citrix. By June 2016 ContainerX became widely available to the public in both free trial and paid versions.
This service offers an all-in-one platform in which the computing, orchestration, networking and storage management is all done in one place, providing a single area for all containers within one enterprise. This service is designed to function with both Linux and Windows operating systems as well as physical and virtual machines alike on a private or public cloud basis.
The general goal of the container standards service is to make an IT administrators’ life much easier. This is done by linking all of the administrator’s software containers together, providing an easy user interface in which they can control all of them at once, therefore saving a great deal of time and personal hassle that can be easily avoided through this service. ContainerX also offers APIs which are Application Programming Interfaces. These APIs allow a business to integrate the all-in-one platform into their very own management portals, allowing for a great deal of self-customisation.
ContainerX boasts several innovative key features. One such feature is the inclusion of elastic container clusters. These clusters allow a business to create a highly elastic infrastructure of software containers. This creates a highly resilient and reliable system that has resource isolation as well as specific pools of resources.
This is very helpful in the event that a container becomes corrupted as the resources are able to be isolated from the other containers, minimising the damage by cutting off the infected container before it can spread to the others around it.
It is widely acknowledged that the vast majority of modern companies use software containers when transferring and storing their copious amounts of data. Many more large and small companies are said to still be on their way to using them. This means that it is so important now, more so than before, for companies to have their own programs that can easily manage their large amounts of software containers. It is simply just not feasible anymore to manually manage all of the software containers that are required by modern businesses.
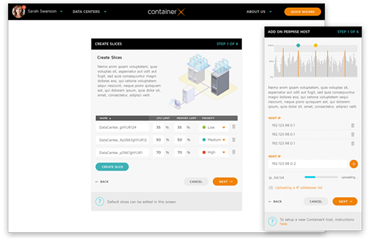
Newer programs, such as the one provided by ContainerX, allow companies to have a much more customised approach to their own software container management. Programs like these are now being used to create and change infrastructure at will, store information easily and move that information from database to database within a moment’s notice. Overall, programs such as these help large companies out a great deal, making their IT department’s work a lot easier by removing the great hassle of manually configuring each container by itself.
As can be expected with a company of such high regard as ContainerX, the security that they provide is of the highest standard. ContainerX includes several state-of-the-art security countermeasures that are sure to protect a businesses’ software containers against malicious programs and other such vulnerabilities that could cause a severe data breach, something which no company desires. One such security measure is that of managing any and all vulnerabilities at the container image stage. Container images are the building blocks of a container.
 These images can be taken from many places online such as on public domains or in more trusted places such as Docker, where they are paid for. Public domains are, of course, much riskier than those that are present on a paid-for site as the free container images very rarely do any security searches before hosting them on their site. This means that that your downloaded container image could very well contain a virus or another piece of malicious software that could jeopardize all of the software containers that are present and connected to each other.
These images can be taken from many places online such as on public domains or in more trusted places such as Docker, where they are paid for. Public domains are, of course, much riskier than those that are present on a paid-for site as the free container images very rarely do any security searches before hosting them on their site. This means that that your downloaded container image could very well contain a virus or another piece of malicious software that could jeopardize all of the software containers that are present and connected to each other.
ContainerX scans these container images immediately and will flag up and report and signs of vulnerability within them, no matter how small. This gives the administrator full power over what they then choose to do with said vulnerable container. This allows the security of the container to be intact by the time it is ready to receive important data, ensuring that a data breach does not occur due to any issues with the container image.
As of September 2016, ContainerX was acquired by Cisco Systems. Cisco Systems are an American-based technology conglomerate that develops, creates and sells their very own networking hardware and software products as well as offering various high-technology services and providing improvements to telecommunication equipment. Cisco is known as the largest networking company in the entire world and has been steadily growing since its inception in December of 1984. Cisco primarily focuses on providing its customers with high-end technology and specializes in creating new ways of networking and sharing digital/virtual information. Cisco’s hands-on approach and ContainerX’s ideology are the perfect match.
Virtualization technology utilizes virtual machines such as public or private “clouds”. These virtual machines transfer packages via wholly separate operating systems. If a virtual machine was trying to transfer three separate softwares then it would require three completely separate operating systems to run at the same time as well as a hypervisor.
In contrast to this, multiple containerized applications all use the same operating system at the same time. For instance, if a physical machine was trying to transfer three separate containerized softwares then only one operating system would be used, being shared by all three. This means that a containerized approach is much lighter than that of a virtual approach and it also uses fewer resources overall, making the containerized approach a much more efficient process.